
Identity Guard
Highly scalable system for filtering, fraud detection and enrichment of data from Telco's signaling data
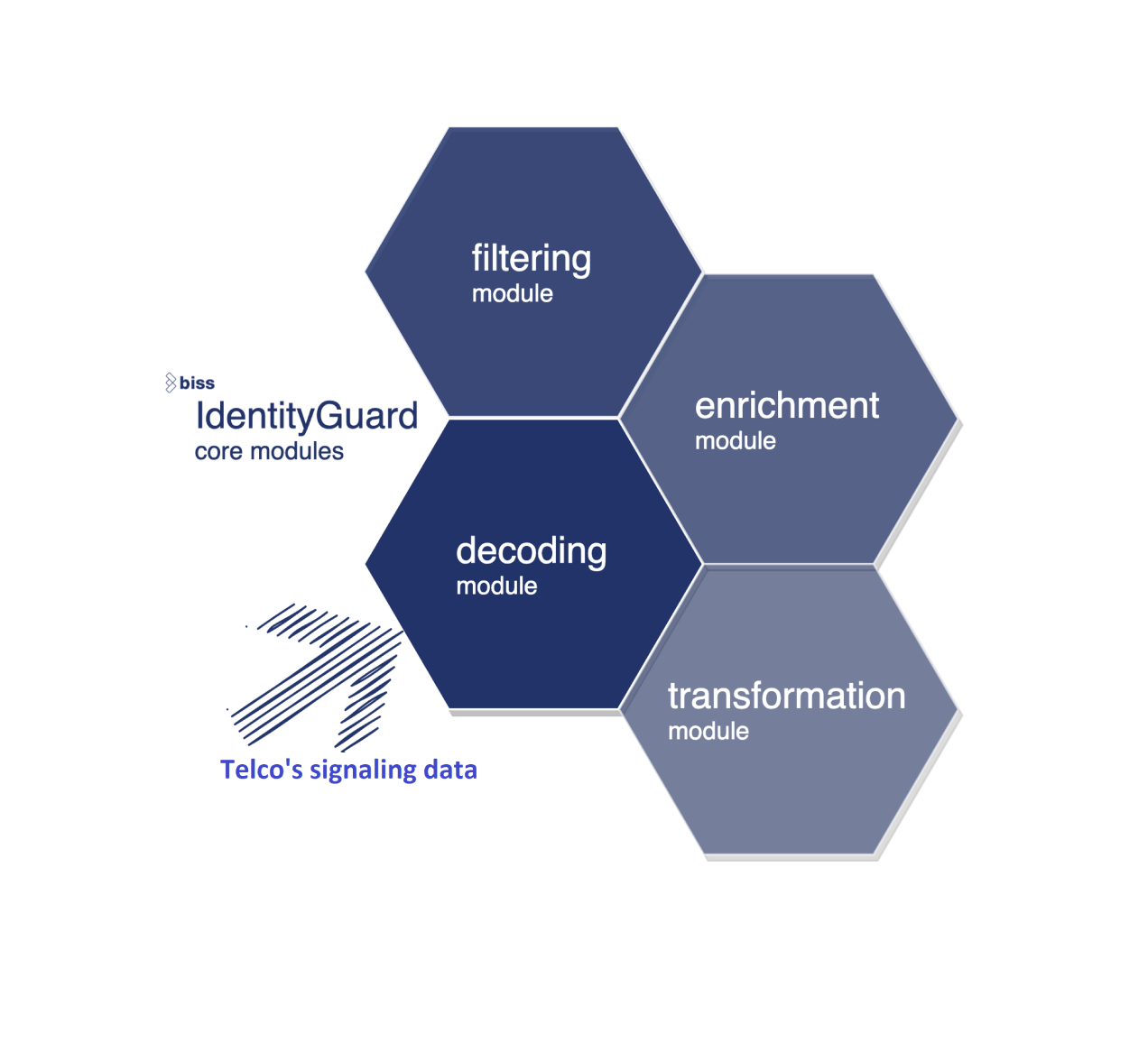
Identity guard
Identity guard is an adjustable set of services that perform data processing in real time.
It has been refined in several software generations with the objective to improve system performance and throughput. Main steps in the process are data ingestion, data processing and data delivery.
Data ingestion includes collecting data from various sources like TCP/IP streams, CSV files or databases. Data processing consists of the steps like parsing, enrichment, anonymization, filtering and formatting. At the end it delivers data to target systems.
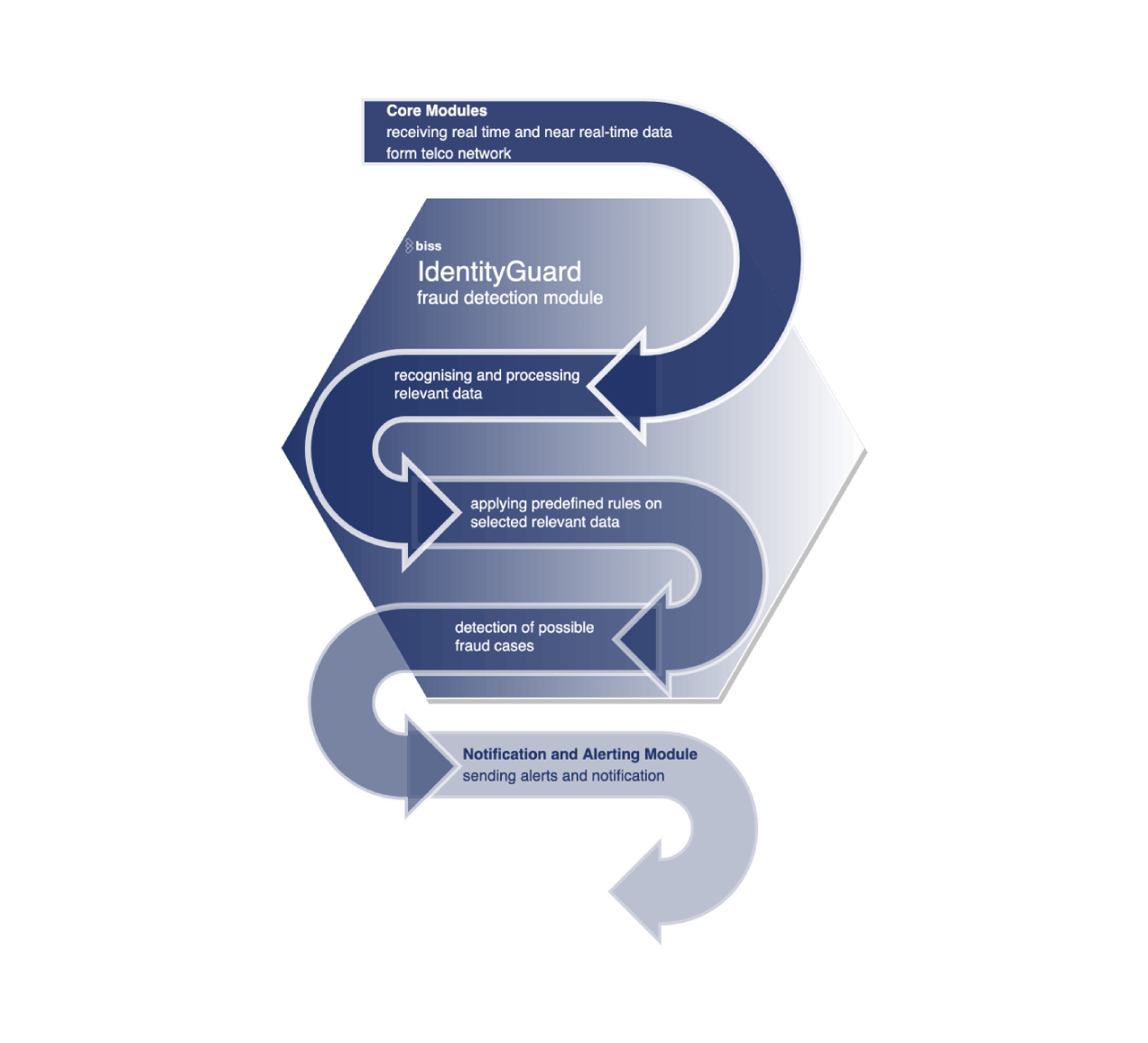
FRAUD DETECTION MODULE
According to a Europol’s Europian cybercrime centre, fraud costs the telco industry around €10 billion per year and the amount rises constantly.
In 2020 SMS phishing attacks skyrocketed by more than 328%. Fraudsters use different methods which target both MNOs as well as customers and vary from infrastructure attacks to social engineering attacks.
Wangiri attacks
Zero-duration calls, mostly to mobile devices, that leave a missed-call number, which is either a premium rate number or one that produces advertising messages
In more recent cases, bots or scripts initiate fraud by filling out a company’s online form with information that leads the companies to call back premium numbers
Interconnect bypass
Using SIM cards from a local carrier and rerouting international calls using a SIM box or GSM gateway
SMS Spam & Phishing
Sending mass SMS in order to obtain personal information from the person who receives the messages
Adding new rules
Identity Guard supports adding new fraud rules and has support of fraud detection exclusion list
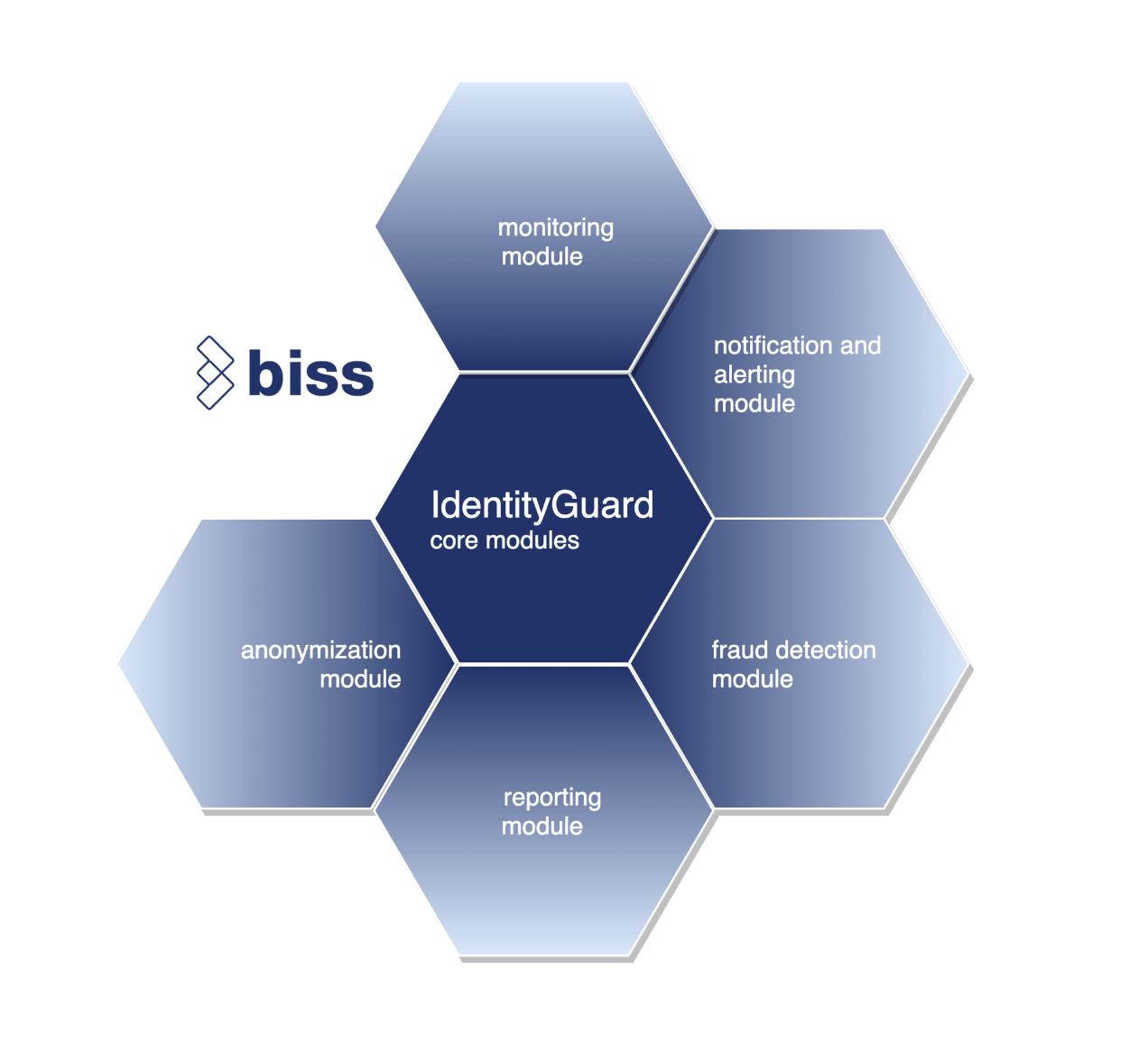
PROTECT PII
Protect personally identifiable information by anonymizationusing token rotation and k-anonymity principle.
Enrich or reduce
Enrich data from other sources (like CRM, billing or other systems). Reduce data sets by filtering with rules, consents or blacklists
Enforce consent
Enforce data owner’s consent for each processing purpose. Include or exclude data based on consent status
Reverse anonymization
Control reverse anonymization of PII data securely
Compliance
Recording all actions and processing providing audit trail ensuring company and legal compliance
Notification and alerting
We will alert you of every fraudulent activity or any other suspicious activities recognized by our algorithms
 Bits of vision
Bits of vision